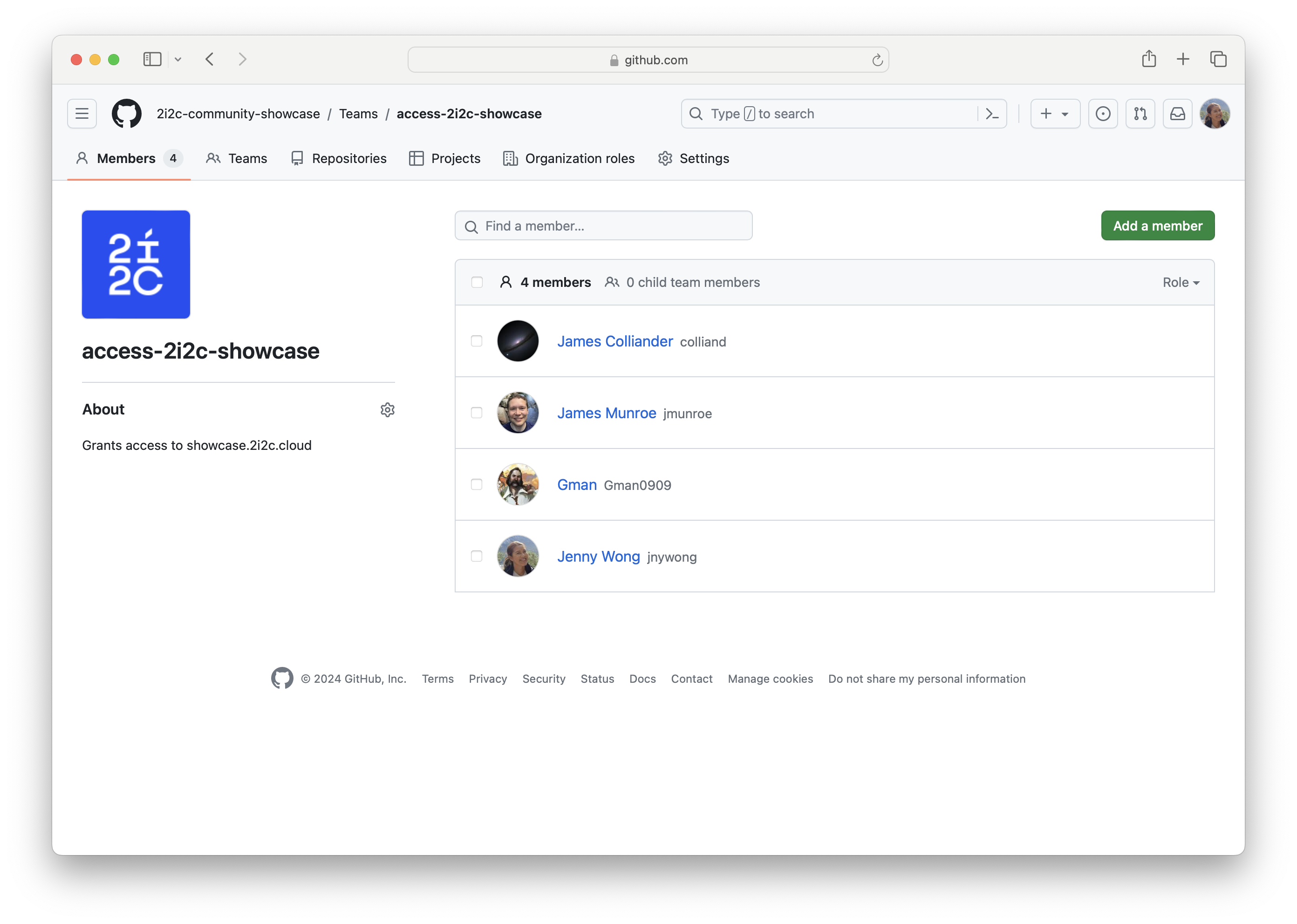
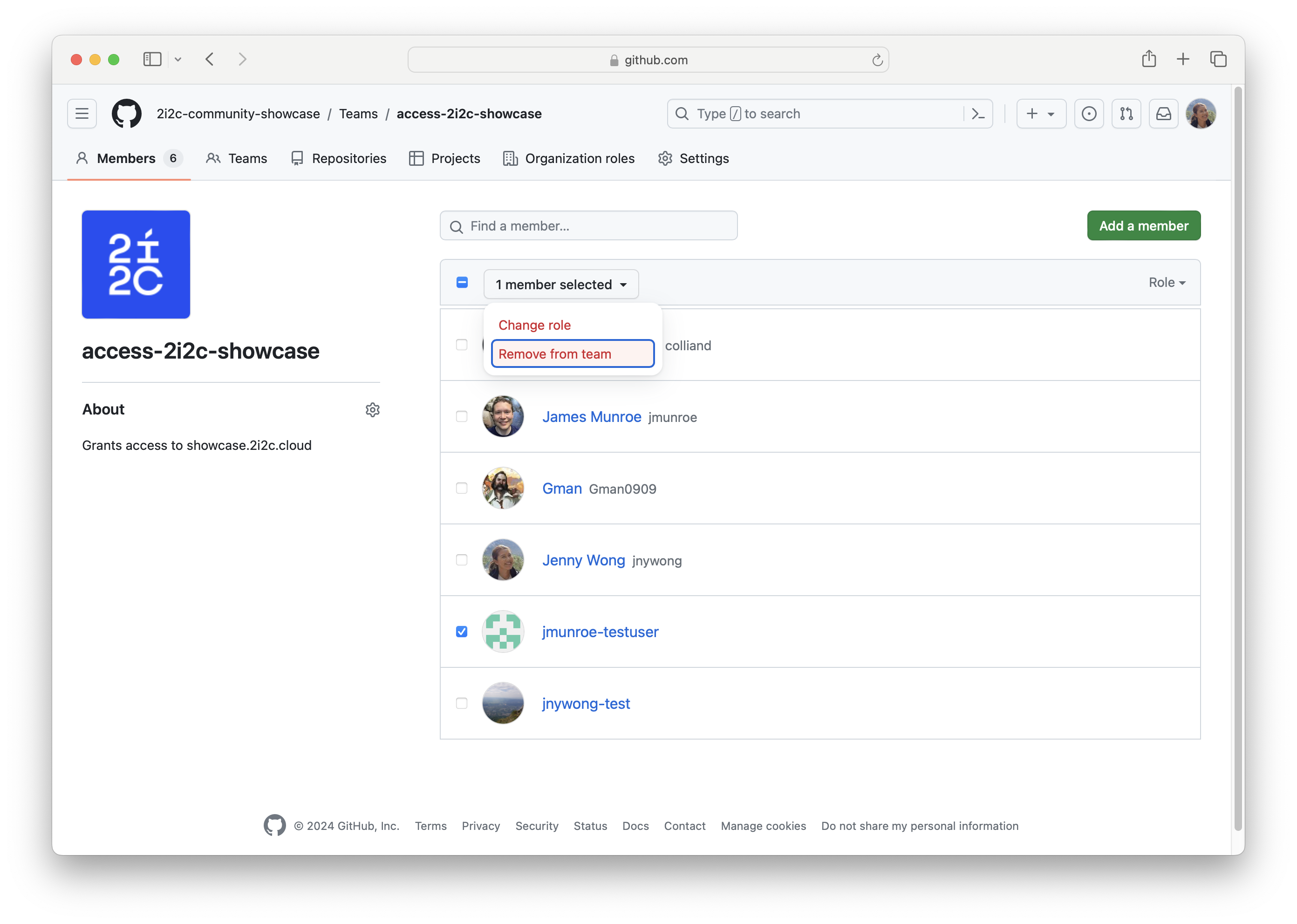
User authentication and access#
Authentication providers#
Users can prove who they are by logging in via an authentication provider. Currently, the following providers are supported:
CILogon#
An extremely popular provider for various institutional logins, Google accounts (including @gmail.com accounts), Microsoft accounts, etc. This is our primary authentication provider. It can support allowing users from multiple institutions to login as well, which is very helpful. 2i2c can manage CILogon using the JupyterHub CILogonOAuthenticator.
Some key terms about CILogon authentication worth mentioning:
Identity ProviderThe authentication service available through the CILogon connection.
When a user logs in via CILogon, they are first presented with a list of various institutions and organizations that they may choose from (
Australia National University,UC Berkeley, etc.).The available identity providers are members of InCommon, a federation of universities and other organizations that provide single sign-on access to various resources.
Note
Check if a community’s login provider is available on CILogon, by going to https://cilogon.org/idplist and filter after its name.
User accountWithin an institution, each user is expected to have their own user account (e.g.
myname@berkeley.edu). This is the account that is used to give somebody an ID on their JupyterHub. This is entered on an Identity Provider’s login screen.
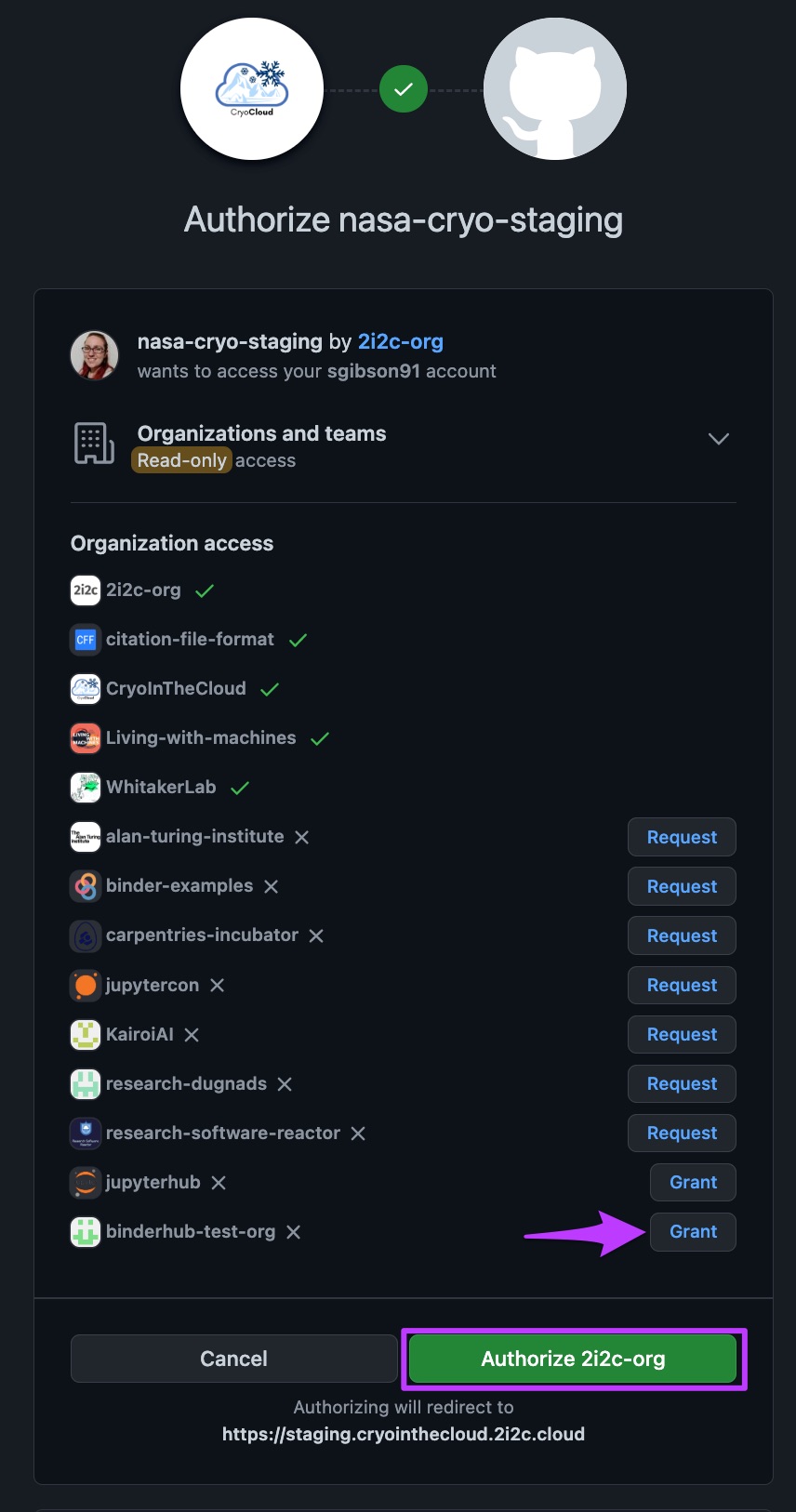
GitHub#
Extremely popular community of people creating, publishing and collaborating on code. Accounts are free, and many people already have them especially since the target community for most hubs are people who also write some kind of code. We can setup GitHub authentication so you can either manage a list of specific GitHub handles in the JupyterHub admin panel, or so that members of a specific GitHub organisation or team are automatically authorised to use the hub.
<a different provider>#
We may be able to support other authentication providers, depending on your specific needs and the provider’s complexity. However, this should be used as a last resort and will come with an increase in management cost, to offset the extra engineering complexity. Please reach out to us if none of those above work for your use-case.
We will ask you what provider you want when we set up the hub. We can change the provider after the fact, but only if absolutely necessary.
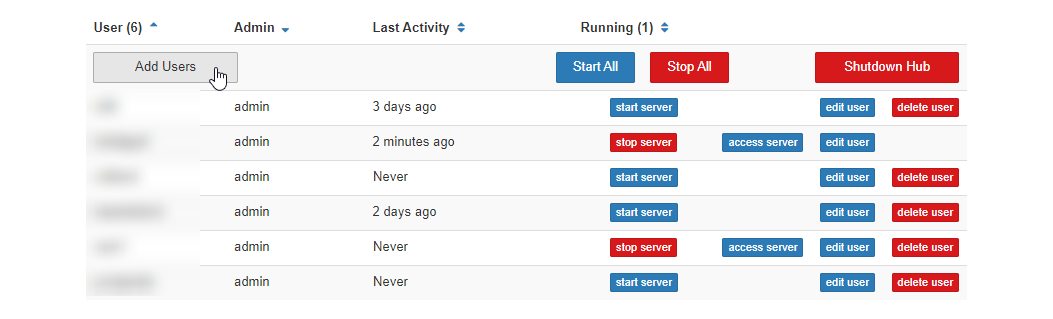
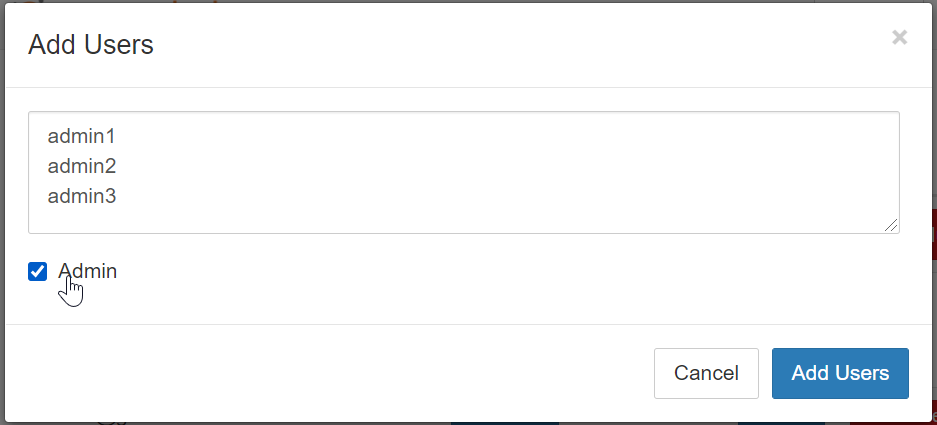
Finding usernames#
Usernames are assigned depending on the kind of authentication provider your hub is using. In general, it matches whatever the visible ‘username’ in your authentication provider is. The table below lists the available providers, and how to determine their username.
Provider |
Username |
|---|---|
CILogon |
Email address |
GitHub |
GitHub user name |
Debug user authentication issues#
CILogon#
If users are running into strange errors when they log in (for example CILogon error pages that say “Looks like something went wrong!”), ask them to try these steps in debugging:
Try logging in with an
incognitowindow. This will help determine if their issue is due to some cookie / cache that is stored on their machine.Ask them to clear their cookies / cache for all CILogon websites. For example, here are the Google Chrome instructions to clear cookies.
If using
CILogon, double-check that they’ve signed in with the correct account, and ask them to switch accounts if needed.

 icon is located next to each member account.
icon is located next to each member account.